Penetration Testing
Pentest created to simulate real-world cyber threats against
your organization, keeping your defenses rock-solid in the process
Initiate a quick pen test, led by one of WDP2’s certified in-house penetration testers, equipped with cutting-edge technology, and a proven methodology adhering to industry standards. Expect comprehensive, audit-ready reports delivered promptly and within budget.

The Scope Of our Pentest is Wide, Offering Analysis Across Range OF
Technologies And Organizations.
Our Penetration Testing Methodologies Adhere To Industry Standards,
Incorporating Guidelines From Prominent Sources
Our penetration testing methodologies adhere to industry standards, incorporating guidelines from prominent sources
the Penetration
Testing Execution
Standard (PTES)
Open Source Security Testing Methodology
The SANS CWE Top 25
NIST
We Leave No Loopholes In Your Defenses
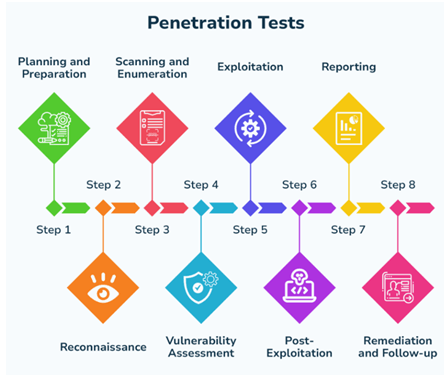
1. Planning and Preparation
2. Information Gathering
3. Enumeration
4. Vulnerability Analysis
5. Exploitation
6. Post-Exploitation
7. Reporting
8. Remediation
Why Do You Need a Pentest?



Overall organizations require penetration testing for several pivotal reasons:
- Making significant alterations to infrastructure necessitates pentesting to identify and address security vulnerabilities proactively.
- When launching new products or services, pentests guarantee potential weaknesses are identified before exploitation by attackers.
- During business mergers or acquisitions, pentesting safeguards against security gaps arising from system integration.
- Preparation for compliance with security standards such as GDPR or PCI DSS involves pentests to ensure regulatory adherence.
- Pentesting serves as a testament to the organization’s commitment to data security when bidding for large commercial contracts.
- Utilizing or developing custom applications necessitates pentesting to identify and remediate vulnerabilities, safeguarding critical assets and data.
Benefits Of Penetrating Testing
- Protects Your Revenue Stream
- Proactively Identifies Vulnerabilities
- Offers Unbiased Security Assurance
- Strengthens Existing Controls
- Compliance With Regulatory Requirements
- Ensures Business Continuity
Our Penetration Testing Services
External Network Penetration Testing
Our external infrastructure penetration testing involves a trusted and seasoned security consultant assessing the security of externally facing networks and systems. This thorough examination aims to uncover vulnerabilities and weaknesses that could potentially be exploited by real-world adversaries. By simulating cyber attacks from outside your organization, this testing ensures your defenses can withstand genuine threats. Specifically, it evaluates the security of your publicly facing infrastructure to determine if attackers could breach your network through services on your external-facing IP addresses. This includes testing the security of firewalls and VPNs, identifying connected devices and the services they offer, and conducting independent research to uncover vulnerabilities. Our ultimate goal is to exploit these vulnerabilities to assess the resilience of your network against potential intrusions.
Internal Network Penetration Testing
Our internal network testing mimics insider threats by probing for vulnerabilities within your organization. It plays a crucial role in thwarting data breaches, ensuring that if external defences falter, internal safeguards remain resilient in protecting sensitive data. By simulating scenarios involving rogue employees, contractors, guests, or malicious software, such as viruses or malware, we evaluate the potential impact on compromising internal hosts. An attacker with insider access could exploit these vulnerabilities to gain unauthorized access, steal confidential information, disrupt services, or tamper with the integrity of data, including financial transactions. T The goal of internal infrastructure penetration testing is to assess the security of critical internal networks and identify weaknesses that could be exploited by real-world adverseries.
Web Application Penetration Testing
Our web application testing meticulously examines your application's code to uncover security vulnerabilities, mitigating the risk of exploitation by attackers. It pinpoints intricate flaws like business logic issues, injection vulnerabilities, and privilege escalation vectors. In today's landscape, web application vulnerabilities are often at the center of major data breaches. Moreover, a compromised web application can serve as a platform for stored cross-site scripting (XSS) attacks, posing a threat to every visitor's browser on your site. These vulnerabilities pose significant risks to your brand and reputation if left unaddressed. Our web application penetration testing, conducted by a trusted and experienced security consultant, involves a comprehensive security assessment of your web application, website, or web API. It uncovers vulnerabilities that could potentially be exploited by real-world adversaries, providing valuable insights into strengthening your application's security posture.
Mobile Application Penetration Testing
Mobile application penetration testing involves a thorough security evaluation conducted by a trusted and proficient security consultant. This assessment encompasses both iOS and Android mobile applications, ensuring comprehensive client, data transit, and server-side scrutiny for applications developed across various platforms, including iOS, Android, and Windows 8. Our methodology is rooted in OWASP guidelines, encompassing approximately 100 distinct tests covering client-side devices, data transit, and server-side APIs. Our rigorous testing regime addresses the OWASP Top 10 2016 mobile risks, targeting the most critical and widespread security vulnerabilities identified by industry consensus.
Wireless Network Penetration Testing
Wireless testing is vital for uncovering security vulnerabilities in your Wi-Fi networks, preventing unauthorized access and safeguarding your internal network from intrusion. It ensures that even your neighbors aren't eavesdropping on your activities. As wireless technology becomes increasingly widespread, it often lacks proper security measures against common attacks. Inadequately secured wireless networks serve as easy entry points for unauthorized access to corporate or private networks, especially vulnerable from remote locations beyond an organization's trusted perimeter. Our expertise extends to conducting penetration tests on various wireless technologies, including WiFi, Bluetooth, and other radio transmissions. Wireless penetration testing is a proactive security measure crucial for organizations to assess and mitigate vulnerabilities, safeguard sensitive data, adhere to regulatory requirements, and uphold robust security standards in an era heavily reliant on wireless connectivity
Social Engineering Testing
Social engineering entails manipulating individuals using psychological tactics to gain unauthorized access, acquire confidential information, and execute actions that jeopardize an organization's security. Integrating social engineering assessments into your security strategy allows for a deeper understanding and mitigation of human-related security vulnerabilities frequently exploited by adversaries. These attacks leverage flaws in human psychology to deceive authorized personnel into unwittingly fulfilling requests from adversaries. While they manifest in various forms, the most common include phishing (email-based), vishing (voice-based), and smishing (SMS-based). Our seasoned consultants simulate these attacks through collaborative exercises, enabling your organization to evaluate the efficacy of existing training programs and reinforce the importance of vigilant, security-conscious behavior. These assessments mirror the tools, techniques, and procedures employed by real-world adversaries, tailored to your organization's strategic goals, specific requirements, and technological landscape. Upon completion of a social engineering assessment, you'll receive a comprehensive report detailing the simulated attack results, including all identified vulnerabilities ranked by criticality, along with recommended remedial actions. This proactive approach not only mitigates the risk of data breaches and unauthorized access but also bolsters your organization's overall security posture, minimizing potential operational, financial, and reputational repercussions.
